When you work with anti-detect browsers, it’s crucial to regularly audit your digital fingerprint. This quick guide explains how to properly read data from Browserleaks (and its variants) for optimal setup of WADE X—one of the most advanced anti-detect browsers on the market.
NOTE: This article is for technical education only and does not promote bypassing any platform’s terms of service.
Anti-detect browser with mobile emulation –10% OFF with WHOER
How anti-detect browser works
Anti-detect browsers enable multi-accounting by spoofing and randomizing browser fingerprints, allowing each session to appear as a unique device to avoid anti-fraud detection. Without anti-detect, multi-accounting is quickly blocked due to device fingerprint correlation.
Why fingerprint checking is important
Modern websites use hundreds of parameters—browser version, languages, screen, device memory, and more—to build your unique browser fingerprint. Even if you use proxies or change devices, a poorly configured fingerprint can betray you.
WADE X stands out with a built-in fingerprint uniqueness checker, allowing you to instantly assess how detectable your session is. But for deeper analysis, you can use third-party services such as browser leaks, which give a more technical breakdown of your identity online.
Creating realistic profiles in one click
A key advantage of WADE X is its auto-mode for profile generation. You can create a profile that closely imitates a real device with a single click, thanks to several built-in automatic modes. These modes include desktop and mobile device emulation. For instance, if you want to look like a typical Android phone or iPhone, simply select the corresponding mode—WADE X will generate realistic parameters (user-agent, screen size, device memory, etc.) for you automatically. This not only saves time, but also minimizes the risk of revealing artificial or inconsistent data when checked on browserleaks or similar sites.
Step-by-step: using Browserleak with WADE X
1. Start with profile setup
- In WADE X, either manually tweak parameters (user agent, screen, time zone, WebRTC, fonts, plugins), or use the one-click auto-mode to generate a realistic profile—selecting desktop, Android, or iOS emulation as needed.
2. Run checks on Browerleak
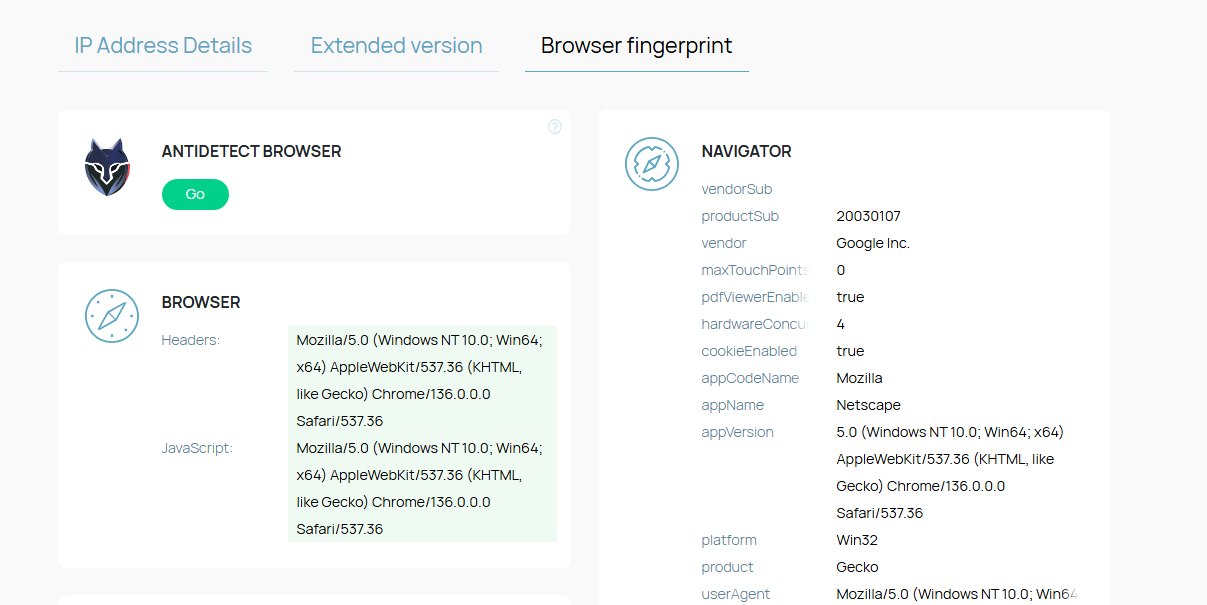
- Open a new session in WADE X using your profile.
- On browerleaks review your IP address first—it should match your proxy, and WebRTC shouldn’t leak your real IP. If brouserleaks reveals your real IP, adjust your WADE X settings, especially WebRTC and proxy configurations.
- Visit the Headers or JavaScript section. Check your user agent, language, and timezone. If browserleaks geo shows your timezone or locale doesn’t match your IP, edit these values in your WADE X profile.
- The Canvas tab checks your canvas fingerprint. If this value is too unique, enable canvas spoofing in WADE X.
- In Fonts and Plugins, make sure you aren’t revealing rare or suspicious data—brouserleaks or browserleaks will highlight anything unusual.
3. Analyze and adjust
- Uniqueness: If browser leaks reports high uniqueness, adjust your WADE X profile for more common settings (change screen resolution, timezone, or plugins).
- Consistency: Ensure all parameters—geo, language, user agent, WebRTC—are plausible and consistent.
- Device Emulation: If you use mobile emulation in WADE X, browerleaks should recognize your device as a genuine mobile device.
Iterate: Make changes in WADE X, retest on browserleaks until no anomalies or suspicious uniqueness remain.
Alternative checker
When you want a simpler summary, use whoer.net for an anonymity score and tips what to fix in your WADE X setup.
Conclusion
Whether you access browserleaks, careful analysis is crucial for configuring anti-detect browsers. WADE X offers both powerful manual controls and convenient auto-profile generation with several emulation modes, including mobile devices—making advanced anonymity accessible in just one click. Combine its in-browser checker with external tools like browserleak for the best results, and check whoer.net for a quick overview. With this approach, you can keep your fingerprint consistent, realistic, and secure.